3 minutes
DigitalOcean firewalls are pretty good
Recently I decided I was going to switch to using DigitalOcean (referral) instead of Online.net, nothing bad on Online’s part, in all honesty I just wanted to play with Laravel Forge and as I was already having to reinstall a server I figured I’d switch to DigitalOcean to save a few coins.
The only downside Forge has though is that it runs all sites as the same system user. No worries, multiple servers instead of one huge beast server it is then!
I’ll have to write up a post on what sort of setup I have for my websites eventually, it’s interesting enough if you’re a nerd and if you’re here on this site you probably are one.
Let’s talk firewalls
I was having a poke around in the control panel looking at all the expensive things like load balancers and whatnot and discovered a freebie - Firewalls! Not just any old firewalls though. Modular firewalls. Cross-region firewalls. Cloudy firewalls!
The thing with this though, and indeed you might be thinking “ugh jeez Cohan you never seen a firewall before?”, you’re able to specify the usual IPs and ranges as you’d hope but also you can specify source and destination droplets and tags too - across regions and everything!
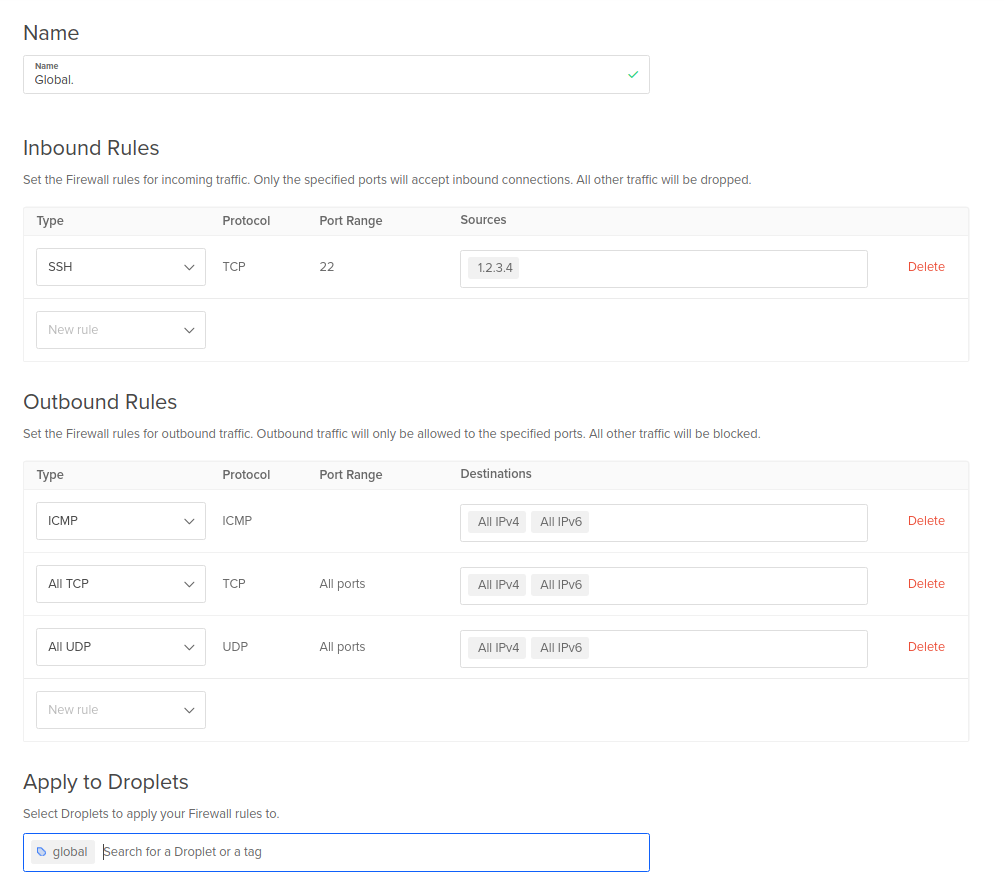
To put that in perspective I’ve tagged all my droplets with a “Global” tag. Now I can create a rule that allows SSH from the IPs I’ll be using, chuck an inbound rule in there for what is effectively “Allow TCP port 22 access to [Global] to a list of my IP addresses”. Boom. All of my droplets block all incoming traffic but allow SSH to my IPs and only my IPs. Sweet! While we’re in what we’re calling a global rule we’ll also allow all outbound traffic here too
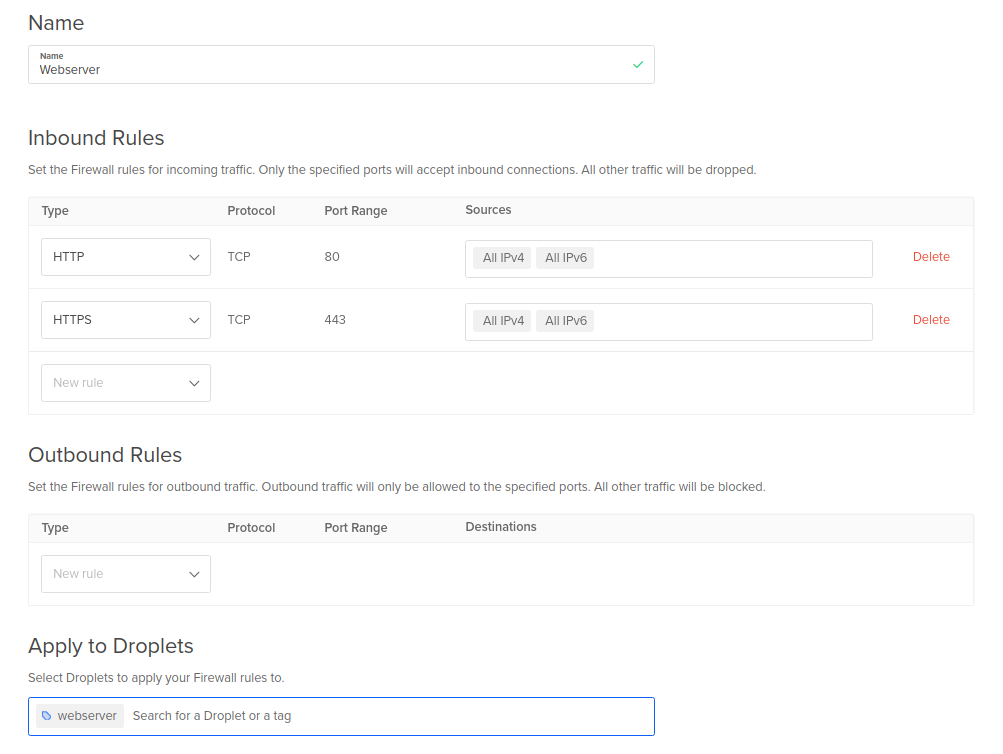
Now then I have a few web-facing servers. Tag them all as “Webserver” and create a firewall rule that is essentially “Allow TCP ports 80,443 access to [Webserver] from [All IPv4],[All IPv6]” - All of the websites come online. London region, Amsterdam region. They’re now blocked off to the world but allow SSH from my IPs and web traffic from the world
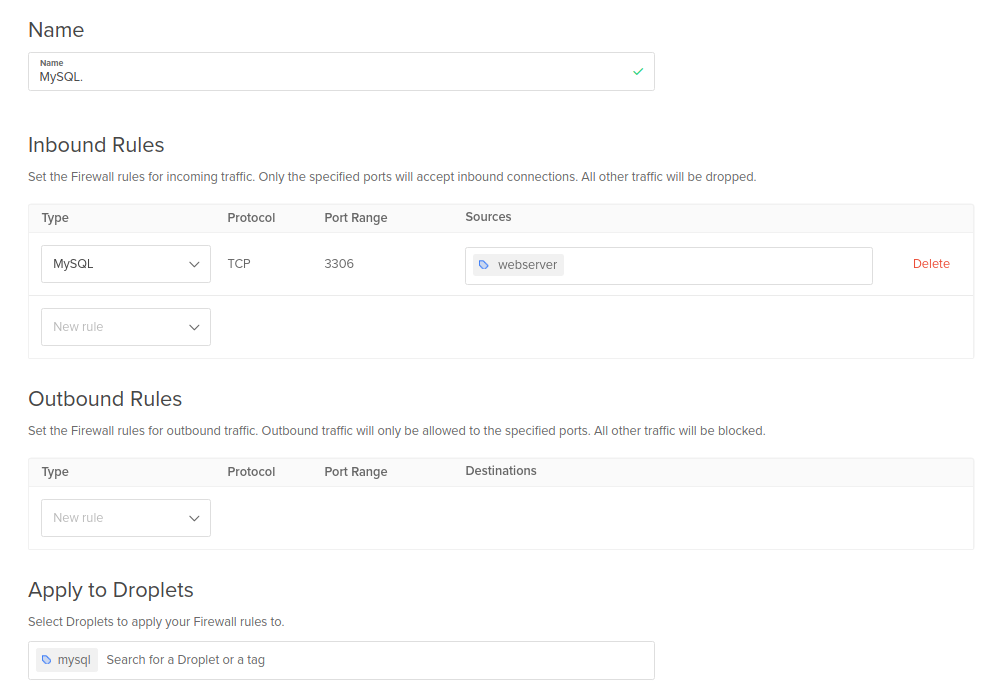
Then we get interesting. I have a separate MySQL server because the websites aren’t very heavy but I wanted a bit more beef behind the backing SQL server. Do I need that sort of setup? Of course not. I wanted it because I wanted it.
Now we set up a rule “Allow TCP port 3306 access to [MySQL] from [Webserver]”. All of the webservers can now connect to MySQL on the SQL server no worries. Even new droplets, as long as I tag them correctly they can connect. That’s awesome right there.
I wish I had some more to say on DigitalOcean’s cloudy firewalls but honestly they’re so easy to use and can be so modular and best of all they just worked. Absolute props DigitalOcean. Love it.